Workforce Identity in 2026: What Attackers Will Exploit Next
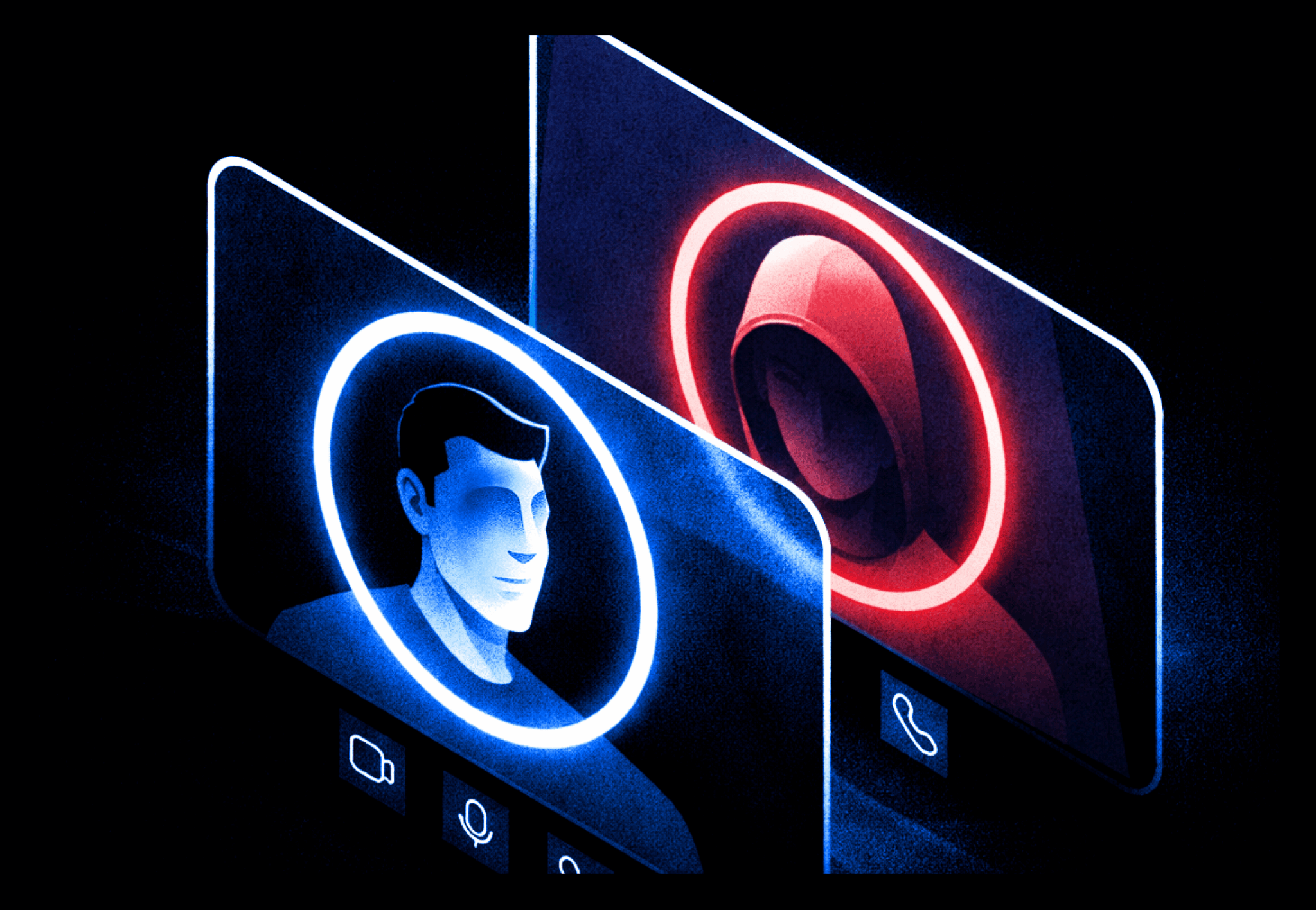

As organizations enter 2026, attackers are not abandoning the tactics of the past year. They are refining them.
The same conditions that shaped 2025 continue to create opportunity. Remote work, cloud-first infrastructure, AI-generated content, and human-centered workflows remain in place. What is changing is the precision and confidence with which adversaries exploit them.
In 2026, workforce identity attacks will feel less like breaches and more like everyday interactions gone wrong.
Deepfake technology continues to improve, particularly in short-form video. In 2026, attackers will rely less on generic phishing and more on targeted impersonation tailored to specific roles and workflows.
Help desks will receive calls that sound like real employees. Managers will hear familiar voices requesting urgent access changes. Hiring teams will interview candidates whose digital presence appears consistent across platforms.
Gartner has warned that by 2028, one in four job applicants may be fake. In 2026, that future will feel much closer.
Rather than focusing only on hiring or initial access, attackers will increasingly target routine workforce moments. Password resets, device reassignments, role changes, and temporary access requests all offer opportunities when identity verification is weak or optional.
These interactions are frequent, time-sensitive, and often handled by staff under pressure to be helpful. When identity is assumed, attackers only need to succeed once.
This shift makes identity risk harder to spot and easier to repeat.
.png)
The organizations best positioned for 2026 are already changing how identity works across the workforce lifecycle.
Instead of verifying identity only at hiring or onboarding, they are introducing verification at key moments when access or authority changes. Identity becomes a reusable signal, not a one-time event.
This approach reduces ambiguity for HR, IT, and security teams without adding friction for legitimate employees.
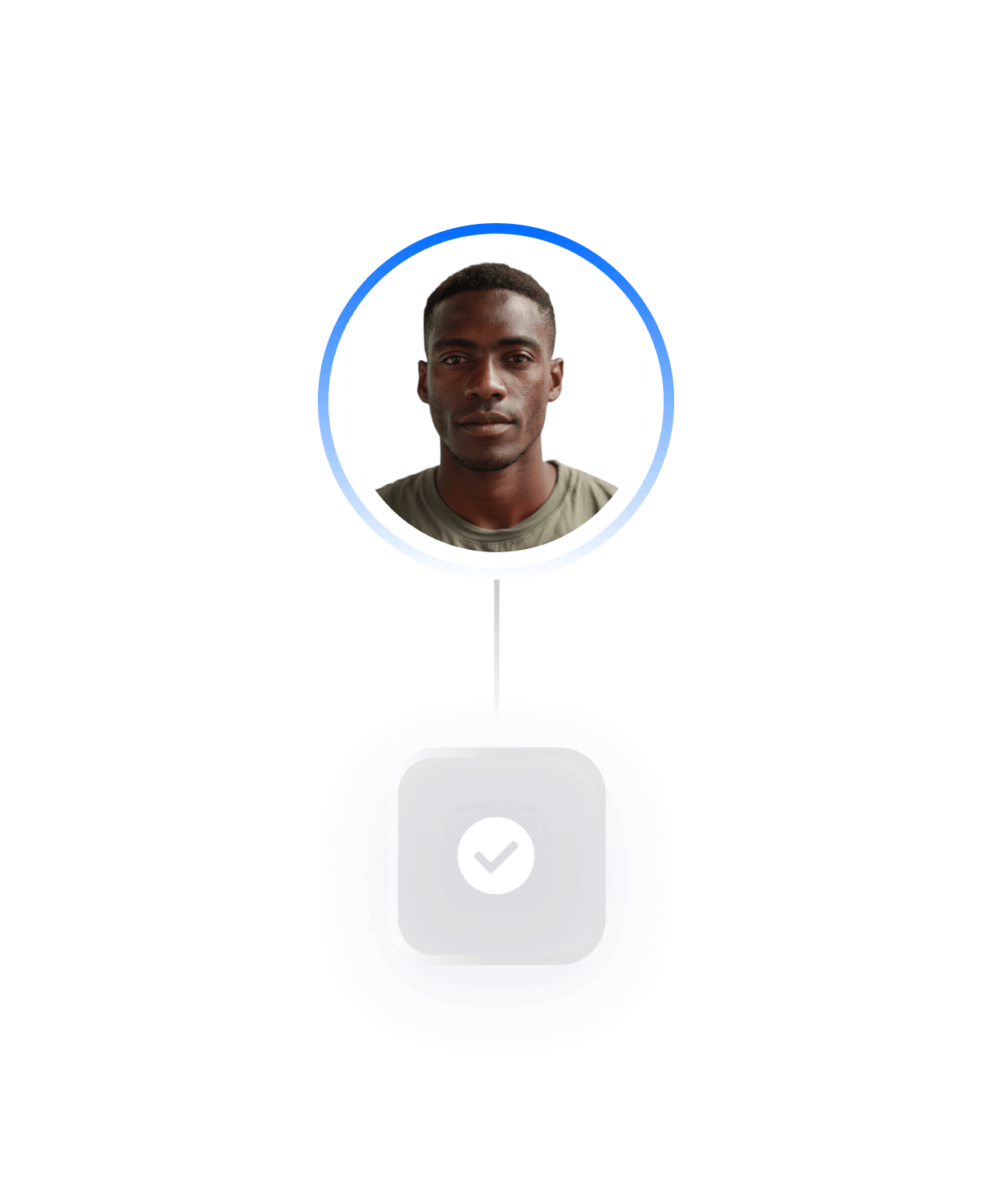
The lesson of 2025 was that identity assumptions are dangerous. The reality of 2026 is that identity verification must be operational.
As impersonation becomes more convincing and social engineering more targeted, organizations will need controls that confirm who someone is, not just what they know or claim. Workforce identity will increasingly resemble how high-risk consumer interactions are already handled.
Organizations that adapt will reduce risk and restore confidence in their internal processes. Those who do not will continue to discover identity failures only after access has already been granted.
Download your complimentary copy of our e-book “Securing the Hiring Process Against Deepfakes and Identity Fraud” to explore:
Originally from India, Harsha Balakrishnan lives in New York City and loves hanging with his dog and all things sports. By day, he works on Incode’s Workforce solution offerings, shaping how enterprises adopt AI-driven identity verification across the employee lifecycle.
Discover more articles, news and trends.