Detect and block repeat attackers
Trust Graph detects duplicate, synthetic, and reused identities across sessions and organizations, without ever exposing PII.
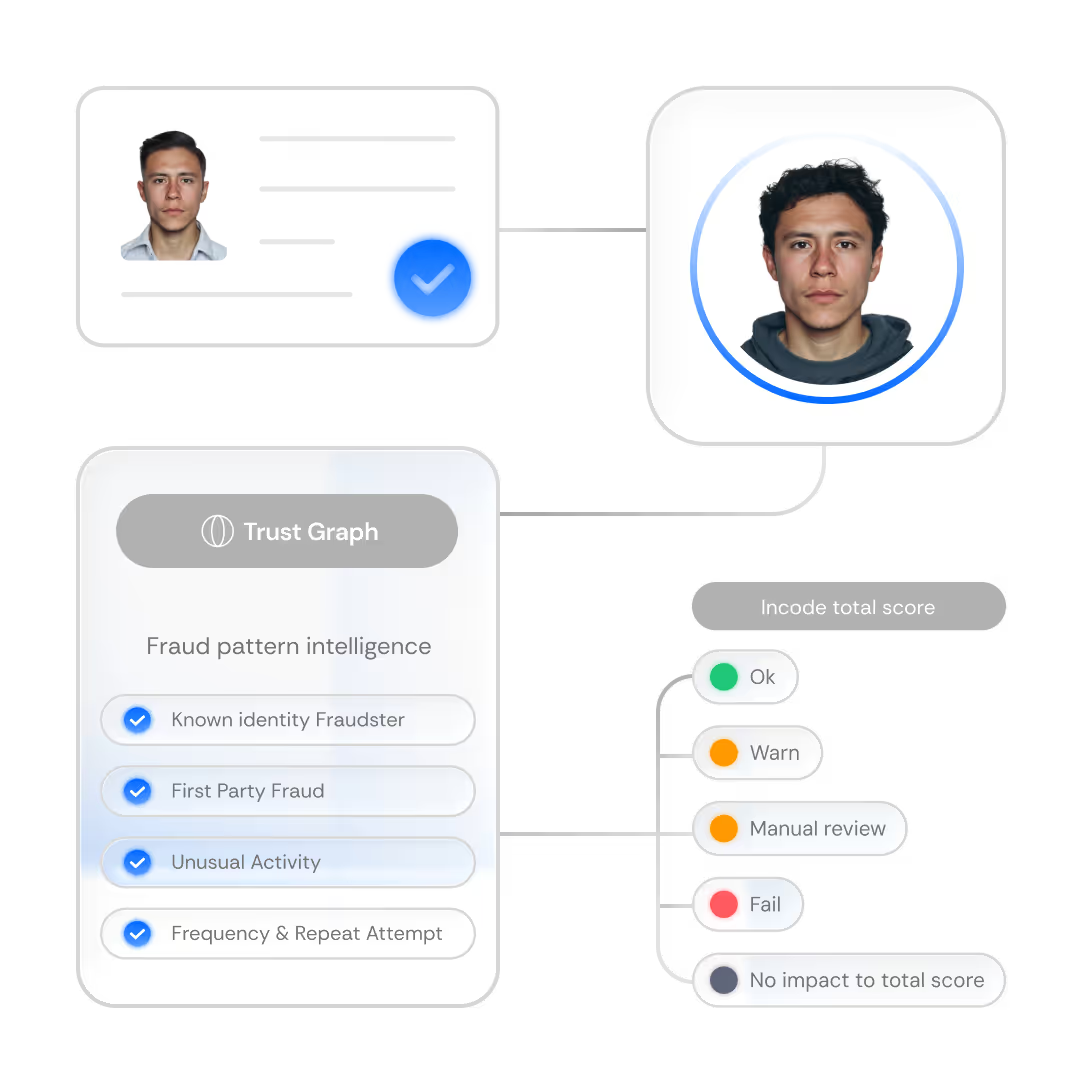
Trust Graph detects duplicate, synthetic, and reused identities across sessions and organizations, without ever exposing PII.

By maximizing a collective defense to flag patterns like duplicate users, reused documents, and synthetic identities, Trust Graph delivers shared threat intelligence and synthetic identities without exposing any PII.

By connecting risk signals across a global network, Trust Graph delivers earlier detection with greater precision. That means stopping more fraud without adding friction for trusted users.
.avif)
Contribute internal signals to Trust Graph to strengthen the network and gain real-time insight into threats flagged elsewhere.
.avif)
Trust Graph protects user data while delivering high-impact results. All risk signals are anonymized to meet the strictest data security and privacy standards.
Move beyond isolated, reactive fraud prevention. Collective risk signals work together to proactively stop threats before they become losses.
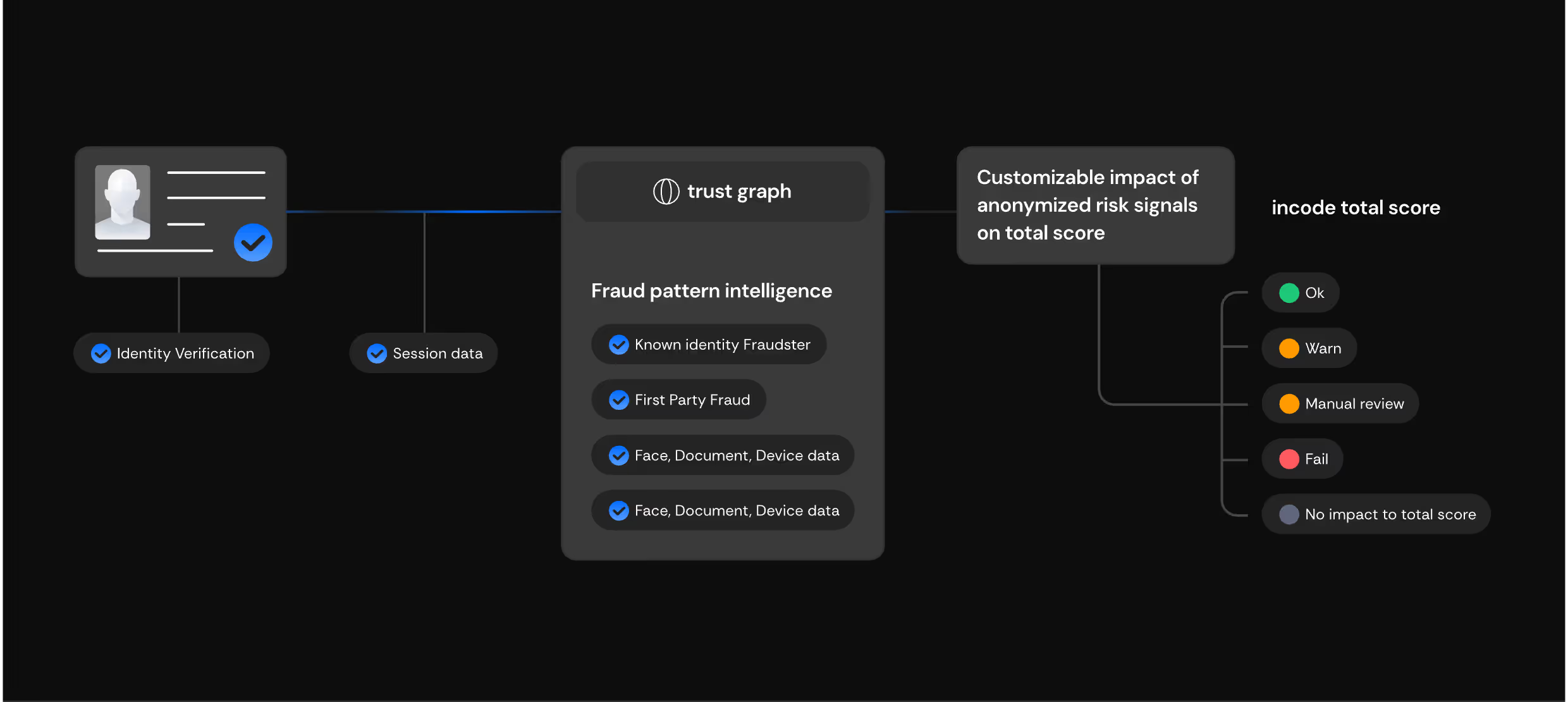
Incode’s technology gives you real-time, relationship-based scoring across a trusted network to stop repeat fraud before it impacts your business.
Trust Graph is fueled by fraud signals from biometrics, documents, behavioral patterns, and device data.
Share fraud signals across a trusted network to strengthen detection and stop repeat attackers reaching your business.
Automatically reassess sessions over time as new risk signals emerge, even after onboarding is complete.
Define and tailor detection rules to match your unique risk sensitivity, industry, and compliance needs.
Gain stronger protection without exposing sensitive data
Verified reviews, certifications, and customer stories show the impact of Incode’s technology.
.avif)
Gain stronger protection without exposing sensitive data.